Projects
There’s a lot more to be seen at the Block Pane Github repository
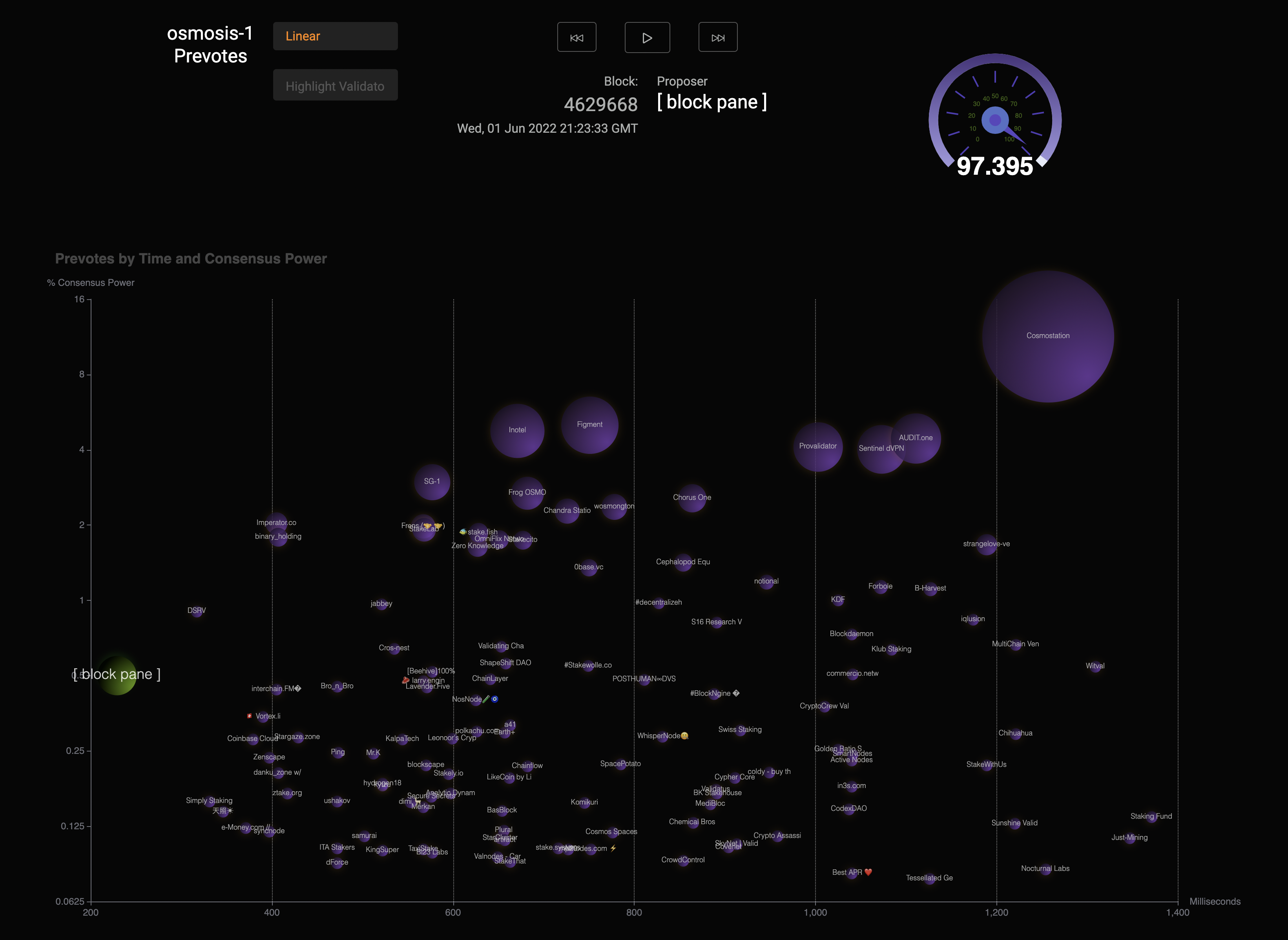
Prevotemon (Alpha)
Live site: Osmosis pre-votes | GitHub
Prevotemon is a real-time visualization of the pre-votes/pre-commit timing for consensus on a Tendermint chain. It monitors/measures via several methods: watching consensus state table, subscribing to consensus events, and finally the committed blocks. This tool is still in development and will likely be integrated with other network monitoring tools soon.
Tenderduty
Tenderduty is a tool for Tendermint validators that will reliably detect missed blocks and notify using Pagerduty. Many new features are in the works.
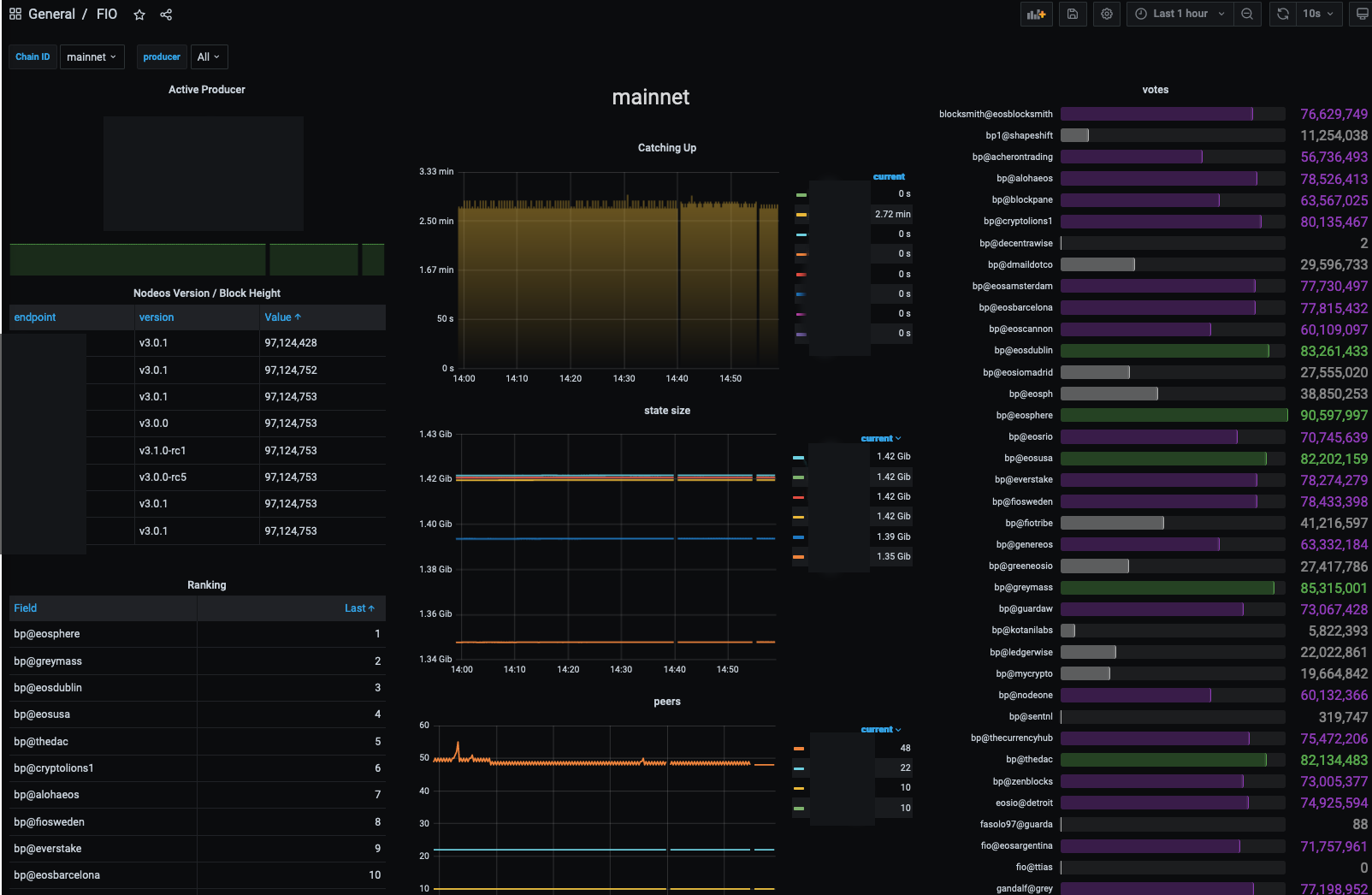
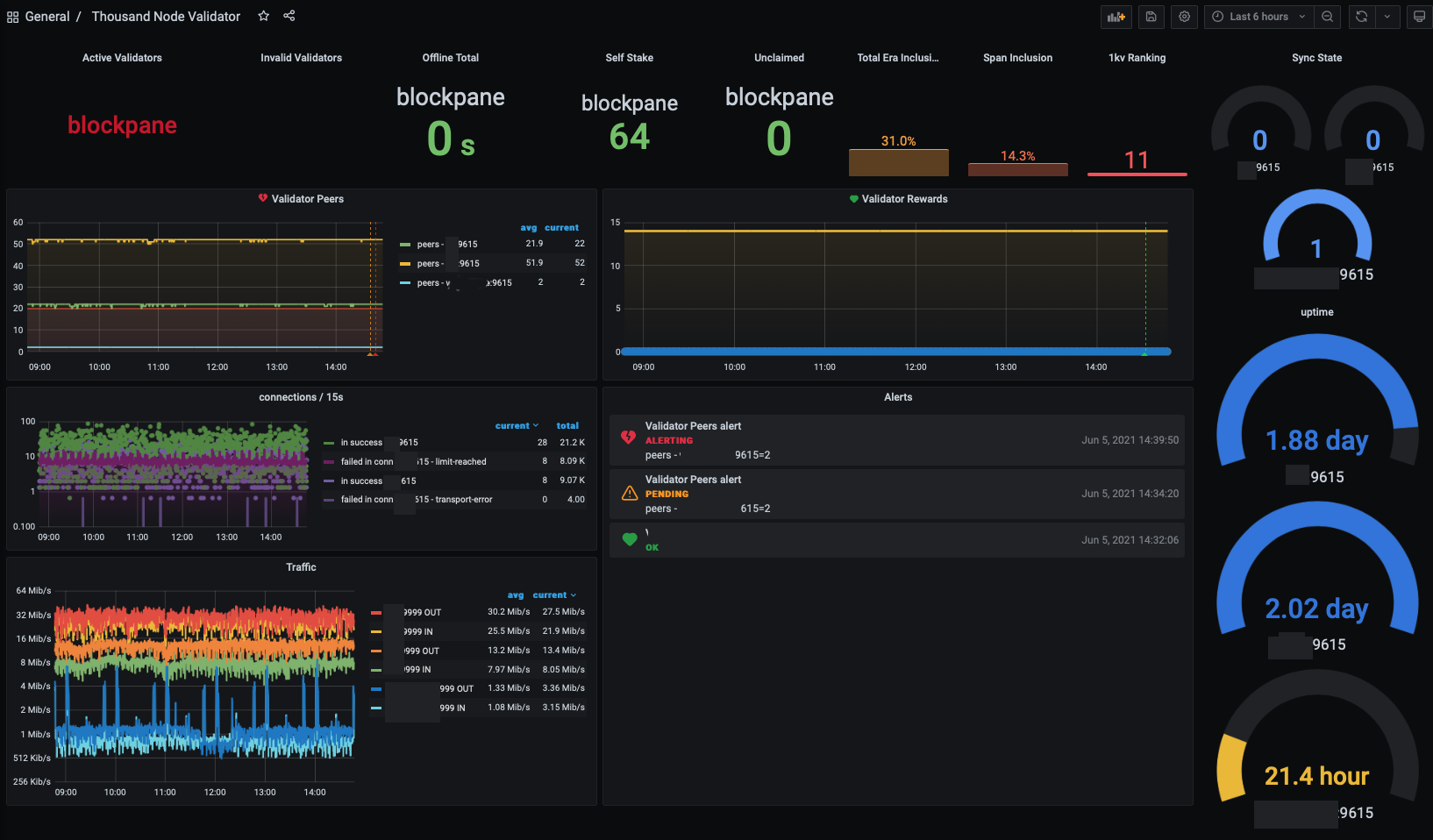
Fio Prometheus Exporter
This is a prometheus exporter for watching multiple FIO nodeos systems. It reports various information about the nodes and block producers.
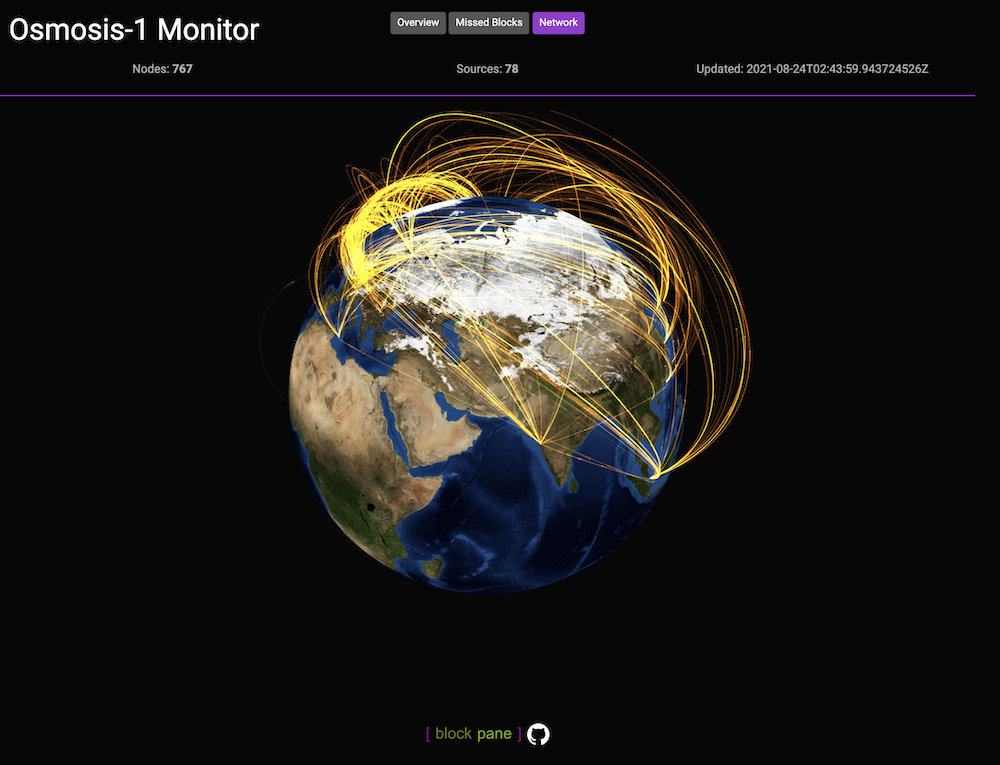
Cosmissed
Live site: Osmosis | Juno | Secret | Terra | Stargaze | Sifchain | GitHub
This is the beginning of a more complex tool for monitoring Cosmos chains. This received a reward from Round 1 of the Hack Juno program.
1KV Prometheus Exporter (inactive)
A simple exporter that scrapes the kusama thousand node validator API every few minutes, and exposes that data as a prometheus endpoint. This project is now inactive since Block Pane has decided to retire from the 1kv program.
The Kusama Foundation generously granted this project a tip and we at blockpane appreciate the support!
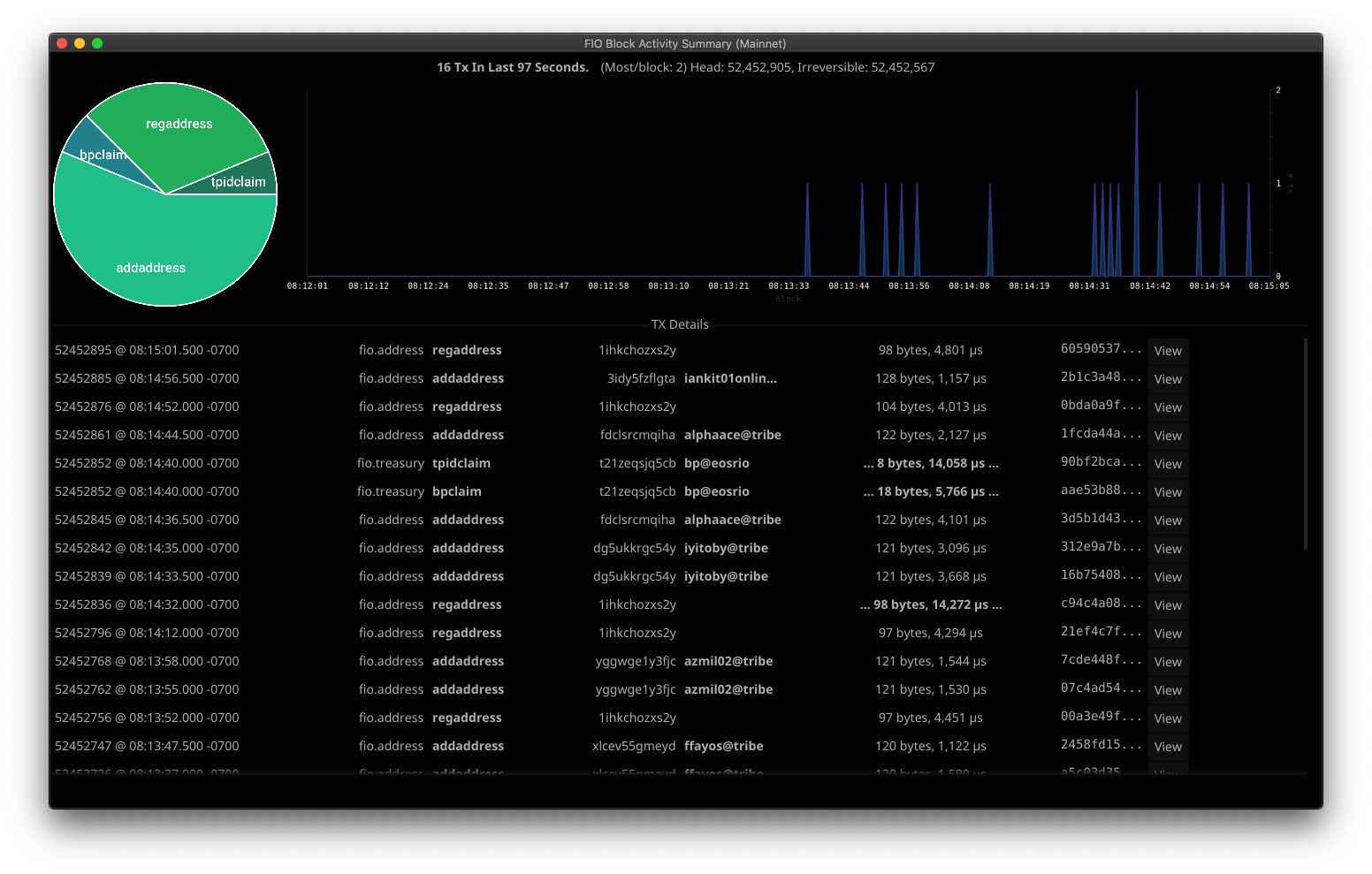
FIO ETL
Live site: graph.fioprotocol.io | GitHub
fio.etl is a project that indexes the FIO Protocol blockchain. It uses EOS Chronicle to
consume blocks, performs various transforms on the data, and stores it in elasticsearch.
It differs from Hyperion in two significant ways, fio.etl does not attempt to provide a history
node alternative, and it performs deeper analysis of the data in a transaction to allow querying
and charting data that is not otherwise possible with Hyperion.
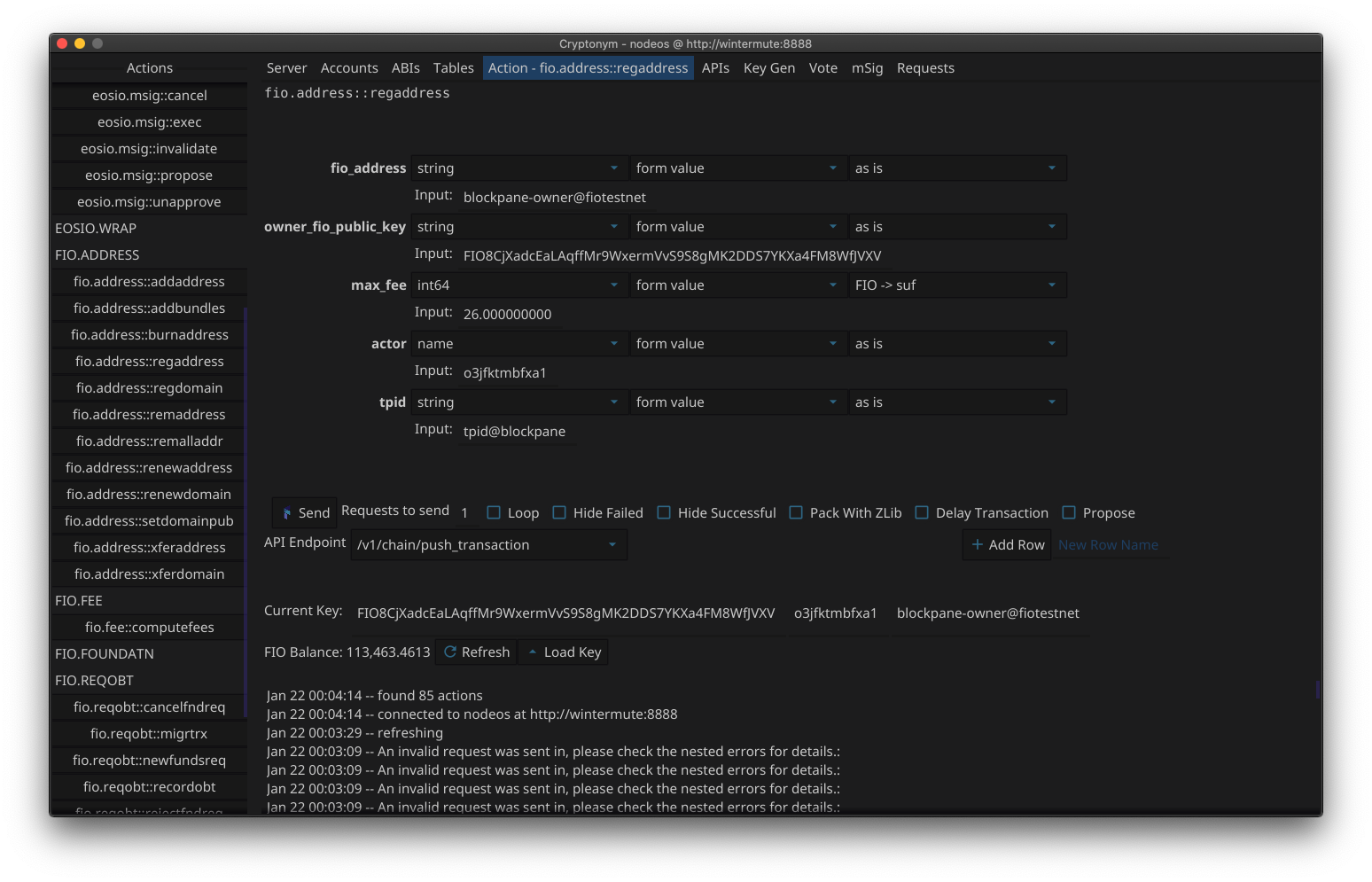
Cryptonym Wallet
- cryp·to·nym | krip-tə-ˌnim
- Definition of cryptonym:
- a secret name [1]
Cryptonym is a development and testing tool for the FIO Protocol blockchain (an EOSIO fork.) Although it is a full-featured wallet, it was designed for penetration-testing FIO’s smart contracts. It employs several unique features that are inspired by web-application pen-test tools. Interactive testing of smart-contracts offers several obstacles, especially around serialization and signing transactions − things that just cannot happen in an off-the-shelf intercepting proxy.
Before releasing the tool it was “de-fanged” removing the most dangerous attack features, however, it is still quite capable: offering several fuzzers, multi-threaded workers, ABI mutation, and other useful testing features.
As a tool for developers it has some convenient features that can greatly assist in interacting with the nodeos APIs, and smart contracts. There are also tools to assist with (advanced) table queries, interacting with the HTTP APIs, and much more.
[1] Source: “cryptonym,” Merriam-Webster.com Dictionary, https://www.merriam-webster.com/dictionary/cryptonym. Accessed 1/22/2021.
Ephemera
Live site: ephemera.link | GitHub
Ephemera is a serverless web-application (AWS: Lambda + API Gateway + KMS + DynamoDB + S3 + Cloudfront) for sharing a secret. It accepts some input that a user wants to share, and generates a URL that can be used to retrieve the secret.
Links are only good once, and up to three layers of encryption can be used. Sure, it’s not an original idea, but almost all of the others are doing it wrong. See the “help” in the application, or visit GitHub for the implementation details.
fio-watch
Fio Watch is a desktop application that monitors the FIO Blockchain (technically it’s capable of working on most EOSIO chains, but attempts to load every ABI at start, so it wouldn’t do well on a general-purpose chain.)
It uses the P2P protocol to get blocks instead of the HTTP Plugin. This makes it much
less intrusive than repeatedly calling get_info and get_block every 500 milliseconds.
fio-go
@blockpane is the maintainer of ‘fio-go’ a Go library based on eos-go for the FIO Protocol.
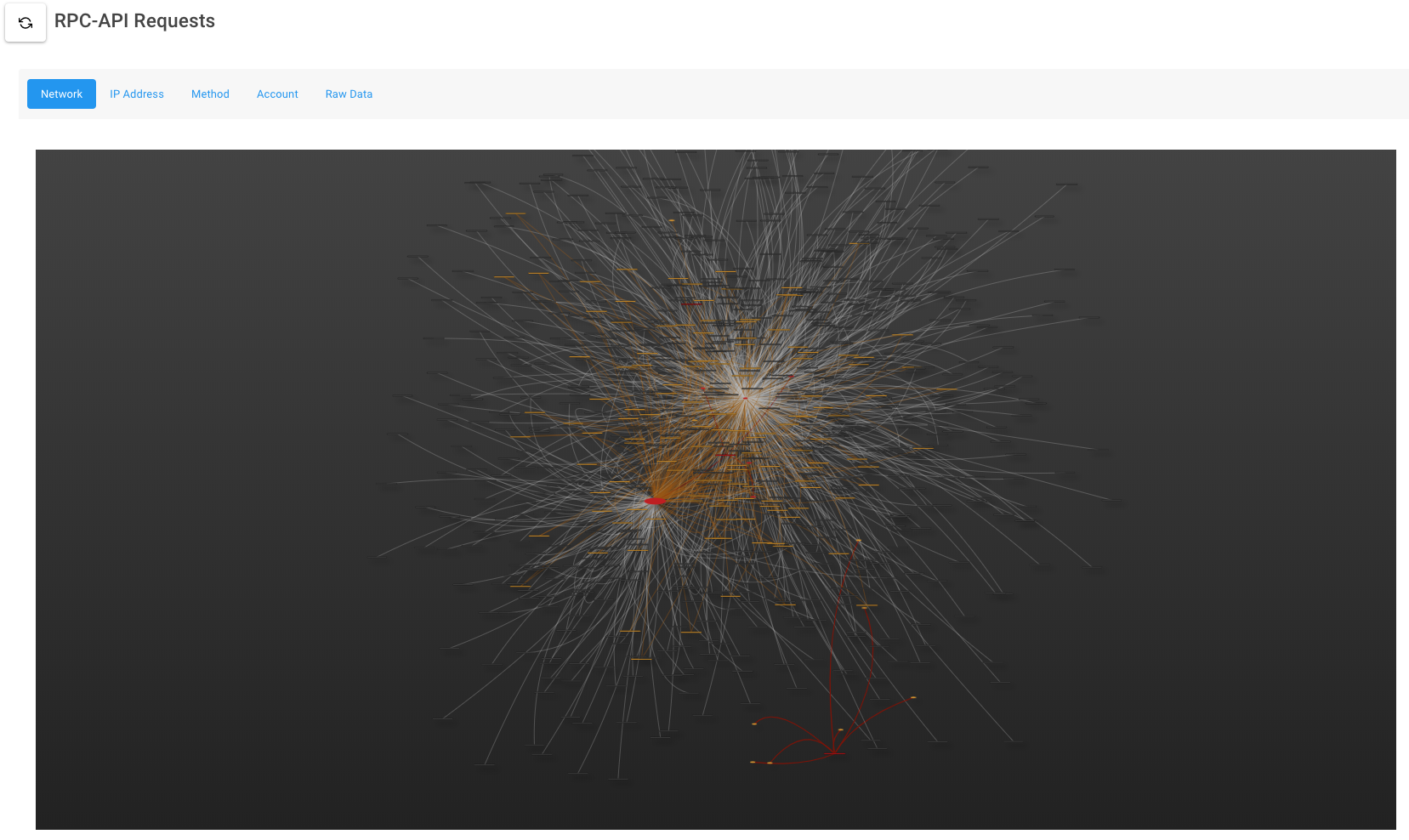
Ethereum Honeywallet (inactive)
A medium-interaction honeypot emulating an unlocked Ethereum wallet.
The honeywallet is a product of the 2019 ethdenver hackathon. It will start a geth daemon, a proxy that rewrites several rpc-api calls returned from geth to fake an unlocked wallet, logs the incoming attacks, and has a simple dashboard showing the data. It includes a network graph that displays the relationships between the attacker’s IP addresses, and ether addresses used.